Cheaters gonna cheat. That’s what the cybercriminals behind a new Fortnite ransomware threat are banking on.
New extortion malware “Syrk” is targeting the world’s most popular video game by posing as a cheat hack for users looking for an edge over rivals. Once installed, it deletes the user’s personal computer files every two hours until a ransom is paid in cryptocurrency to deactivate the malicious program. Luckily there is a simple solution to shut the ransomware down.
Fortnite increasingly targeted by cybercriminals
Fortnite, created by Epic Games, is massively successful with over 250 million players and a very conspicuous fortune of $30 million awarded to the world’s best players in the recent Fortnite World Cup,

The game is a third-person shooter with up to 100 players at a time dueling in a “battle royale” shootout. With players always seeking an edge over the competition, it was only a matter of time before cybercriminals would find ways to use players’ greed against them as a way into their computers.
The Syrk ransomware scheme follows hot on the heels of the credentials-stealing malware Baldr that targeted Fortnite, Legends and CSGo cheaters, as well as the Fortnite database breach.
What is Syrk, the Fortnite ransomware?
Researchers at the security company Cyren say they’ve found that Syrk is in fact not a completely new malware program, but actually a variant of the notorious Hidden.Cry ransomware program that was first uploaded on GitHub in 2018.
Similar to the cryptojacking tool CoinHive, the Hidden.Cry malware seems to have been subsequently tweaked to terrorize a whole new audience and followed in the footsteps of the dreaded Wanna.Cry Bitcoin-blackmailing ransomware.
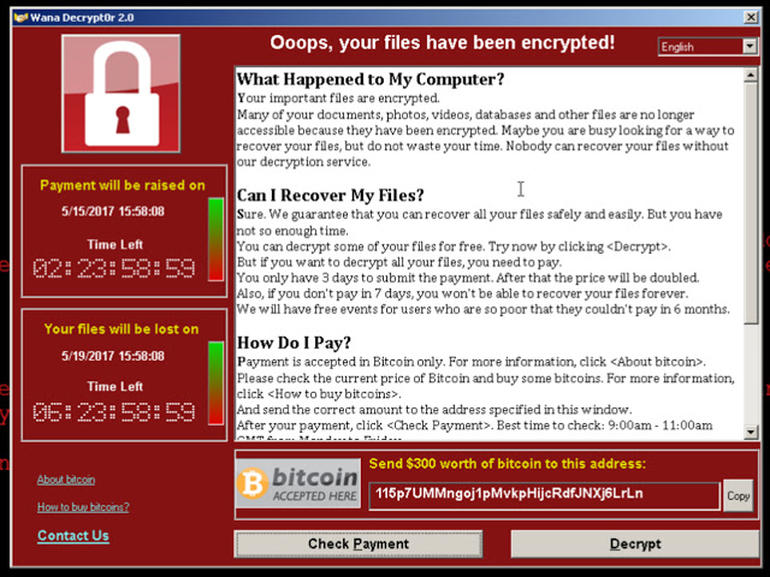
Fortnite ransomware virus is targeting cheaters
Cheaters never prosper, but they help to make crime pay, at least if they cheat on Fortnite, in the form of crypto ransoms to extricate themselves from the situation they put themselves in.
Almost all gaming malware get installed willingly by players desperate to get an edge over their fellow players. The Syrk malware was disseminated on forum boards and P2P file-sharing programs where users quickly downloaded and installed it.
How does the Syrk Fortnite ransomware work?
The Fortnite ransomware virus specifically targets players who want to use a cheat tactic called “aimbotting” (a type of auto-aim), which allows them to create a lock-on tracker on rival players so that they can follow their whereabouts even if they’re hiding behind objects like walls.

Once a player has installed the “cheat hack” file called “SydneyFortniteHacks.exe”, the ransomware will install itself in 10 steps, according to Cyren researchers.
- disabling Windows Defender and User Account Control
- hiding a file that starts looking for specific files to encrypt
- placing the ransomware in the Startup folder to start every time you boot up your computer.
Next, Syrk will encrypt user files and then start a clock timer which will systemically delete user files every 2 hours until the required ransom is paid.
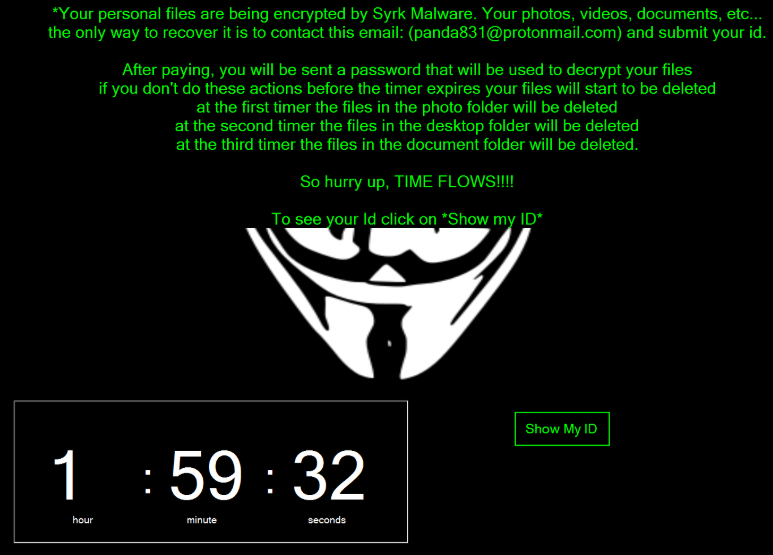
The ransomware will delete the Pictures, Desktop and Documents folders (in that order) every 2 hours until the blackmailer’s demands are met.
Users are strongarmed to contact the hacker (who uses an encrypted Protonmail email account) with the ID provided to them, pay the ransom in cryptocurrency, and wait for the decryption password to be sent to them.
“… (spoiler alert!), this Syrk ransomware is in fact Hidden-Cry with a .Syrk extension. The source code for Hidden-Cry is readily available, having been shared on Github at the end of last year.
One principle feature of the Hidden-Cry ransomware is that, as seen in the instructions shown, is the sense of urgency it creates in the victim by deleting files every two hours. However, we believe it is possible for victims to recover deleted files, given the simple method used to delete the files.”
Cyren Report
How to remove the Fortnite Ransomware virus
Fortunately for Fortnite users, the security industry has seen this trick before, since it’s based on last year’s HiddenCry malware. Therefore, players with infected computers can actually search for a simple text file on their devices that will incapacitate the Syrk hijacker before it starts to erase your precious files.
Cyren states that the malware drops files where you can find both the random ID and the password, in these locations on your computer.
C:\Users\Default\AppData\Local\Microsoft\-i+.txt -> file containing the randomly generated ID
C:\Users\Default\AppData\Local\Microsoft\-pw+.txt -> file containing the password
C:\Users\Default\AppData\Local\Microsoft\+dp-.txt -> file contains ID and password. This will be sent to an email address.”
Once you have extracted the password, use it to decrypt your files, after which a delete.exe file will start running in order to remove the malicious ransomware. As some websites note though, it might be better to let your computer’s anti-virus software take care of it for you (even though they missed it the first time!).
Please note that the Syrk Fortnite virus also attaches itself to any USB drives that might have been connected to your computer, so take appropriate measures with them.
Conclusion:
It’s morally wrong to cheat by using cheap tricks as aimbots. Be the better person and hone your skills through practice. Just kidding.
Once a cheater, always a cheater!
Just know you’re not smarter than hackers and you may be exposing a lot more than just a few photos by unwittingly granting cybercriminals access to your computer.
You might very well compromise the security of any crypto software wallets or sensitive information that could be used against you in a phishing or extortion attempt later. Stay safe out there.
Written by Werner Vermaak
Disclaimer: CoolBitX does not endorse and is not responsible for or liable for any content, accuracy, quality or other materials on this page. Readers should do their own research before taking any actions.
CoolBitX is not responsible, directly or indirectly, for any damage or loss caused by or in connection with the use of or reliance on any content, goods or services mentioned in this guide.
Other Crypto Security Guides by CoolWallet:
Cryptojacking Guide

Phishing Guide