Kraken Security Labs has released a statement on 31 January claiming that their research team hacked the Trezor hardware wallet in less than 15 minutes, due to an “unfixable” device vulnerability that can be exploited by hackers.
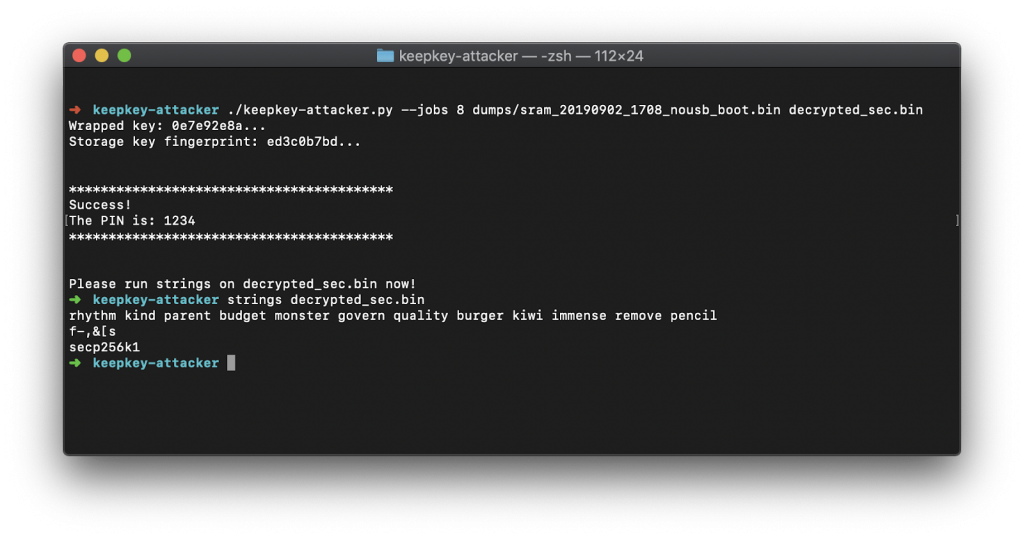
The so-called “Read Protection Attack‘’ is similar to Ledger’s “Seed Extraction Attack” in June 2019. Unlike Ledger though, Kraken revealed how they cracked the Trezor. The vulnerability is also related to the one found in Keepkey, which Kraken’s team breached in December last year.


Kraken Security Labs carry out “ethical hacking” attacks on crypto security companies in order to boost the overall safety of cryptocurrency storage.
In a blog post on their website, Kraken claims they identified a critical flaw in the security of both Trezor models, the Trezor One and Trezor Model T, in October 2019, which can be exploited by criminals.
All that’s needed are equipment of a few hundred dollars (which KSL estimates could be mass-produced for $75 and Ledger previously priced at $100) and 15 minutes of physical access. Kraken alerted Trezor after their findings, and as part of their Responsible Disclosure policy, they are now informing the public to ensure users are safe.
How did Kraken hack Trezor wallets?
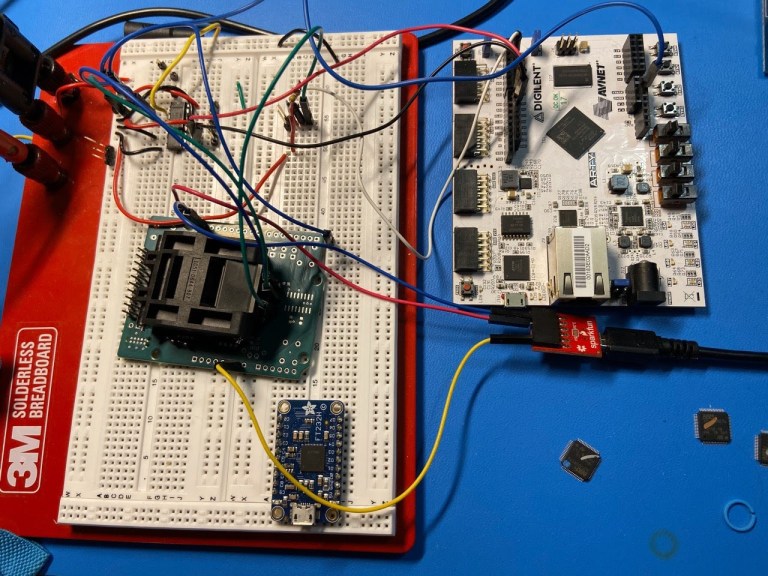
In short, here’s how the security firm did it:
- They used the equipment to build a “glitching device” to extract the hardware wallet’s encrypted seed by attacking the STM32 microchip.
- They then used brute force to crack the encrypted seed (protected by a 1-9 digit PIN) within a few minutes to gain access to the device.
You can also read the full report here, or watch the video below:
Why can Trezor be hacked?
Trezor doesn’t use a Secure Element and therefore their devices are vulnerable to physical hacking attacks where the device is opened and then tampered with.
According to a report by Kaspersky Labs, Trezor only uses a single STM32 chip, a general-purpose microcontroller based on ARM architecture, where they store the private key in its non-volatile flash memory.
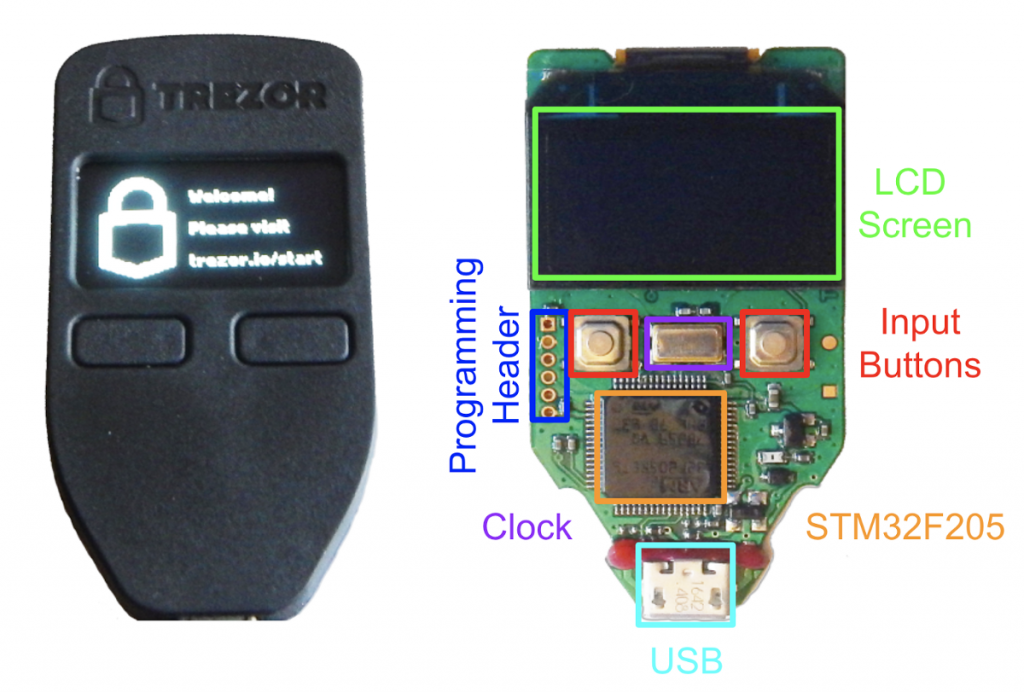
The Kaspersky Labs report also provides details on how to hack Ledger devices. For a step-by-step demonstration of how Kraken did it, check their blog post.
Can the Trezor vulnerability be fixed?
No, according to both Ledger and Kraken. Kraken Security Labs say the weakness is in the microcontroller of the Trezor wallets, therefore it will require a complete overhaul of the cold storage device’s design. Trezor is aware of this weakness but hasn’t made any changes yet.
Kraken suggested in the meantimeTrezor users activate their BIP39 passphrase with a Trezor client in order to protect the wallet, as it’s not stored on the actual hardware wallet.
Trezor’s response to Kraken hack
Trezor is known for not taking criticism lying down. After the Ledger Donjon’s disclosure in March 2019 of several vulnerabilities in the Trezor models, Trezor responded with a strong-worded response, countering with arguments like the “$5 wrench attack” fallacy, stating that it didn’t matter how secure your device was, it only mattered how well you protected your private key and seed passphrase against intruders.
This time, Trezor acknowledged the security attack and the importance of ethical hacking by third parties to help improve the overall security of the crypto industry.

DELIVERED EVERY WEEK
Subscribe to our Top Crypto News weekly newsletter
Trezor, however, remains adamant that hackers will need to be able to physically access the hardware wallet and that it’s the responsibility of users to protect their Trezors and passphrases from prying eyes and hands.
CoolWallet’s Opinion: Use a Secure Element
Our company admires and respects Trezor for their pioneering contributions to the crypto industry and for creating the world’s first hardware wallet back in mid-2014.
However, we do feel the same as other security experts at Kraken, Kaspersky and Ledger, that these exploits are serious vulnerabilities that may put Trezor users’ funds at risk, in situations where physical access to the device is a possibility. It should be addressed.
USB-form hardware wallets can be opened very easily and are therefore vulnerable to both supply-chain attacks (where the device is compromised before it reaches the end-user) or side-channel attacks (where the hacker intercepts or extracts sensitive information on the device).
Therefore, additional security measures should be considered that are resilient to physical hacking attacks.
The CoolWallet S (and other hardware wallets like Ledger Nano ) uses a CC EAL 5+ Secure Element, A Secure Element is the best possible defense against a hack as it locks away the private key and protects it from being revealed to even the device owner. It’s used in traditional finance and banking to protect, for example, bank cards or access keys.
Coupled with a thin form factor (that foils tamper-proof attacks) and water resistance, there’s no need to hide the CoolWallet S at home and worry about who gains access to it. We also have additional safety features, such as physical confirmation by button push on the card and biometric checks such as our App pin code and Advanced Wallet Seed Recovery process.
In addition, the CoolWallet S fits in your real wallet and needs to be within 10 meters from its paired phone to be accessible over encrypted Bluetooth. This convenience and security allow you to take your hardware wallet with you anywhere, without the fear of losing your funds.