During the last few days, a cryptocurrency security issue that many believed had been killed off has once again reared its ugly head(s).
Malicious cryptojacking malware has been found in 11 code libraries for the very popular Ruby programming language, potentially infecting thousands of websites and devices.
Even more brazenly, a Ukrainian power plant has uncovered a massive crypto-mining operation where employees were caught using hardware to mine virtual currencies, potentially compromising the safety of the reactor. Incredible. Did nobody watch Chernobyl on HBO this year??
With a name that sounds like something from a William Gibson novel, what is cryptojacking? How serious a threat is it, and how can it be avoided, or mitigated against? This guide will try and reveal all.
Table of Contents
- What is cryptojacking
- How serious is cryptojacking?
- Why it’s increasing
- The origins of cryptojacking
- Real-world examples of cryptojacking
- Who’s behind cryptojacking
- How to prevent and detect cryptojacking
- How to remove cryptojacking software
What is Cryptojacking?
In short, cryptojacking is the unauthorized and surreptitious use of someone’s computing power to mine cryptocurrencies, without the knowledge or consent of the device owner.
Ever wondered why your computer’s CPU is maxing out at 100% while you’re downloading a torrent or after you’ve visited “certain” sites?
You might very well have been cryptojacked, Jack.
Usually, a cryptojacker will find a way to install malware on a user’s computer or phone, which then uses the device’s processing power and runs a mining program or script in the background, secretly collecting virtual currency mining rewards.

Please note that this character, game or company has no relation to cryptojacking.
Because cryptocurrencies like Bitcoin and Litecoin are pseudonymous by nature, which means they’re not completely anonymous and can be tracked on the blockchain, most bad actors prefer to mine privacy-based coins like Monero (XMR), which is very hard to trace and easy to convert into Bitcoin.
Is cryptojacking a serious security threat?
The “business model” of cryptojacking is quite different from other cryptocurrency security threats.
Unlike ransomware like WannaCry that basically hijacks a user’s computer and forces owners to pay an amount in crypto in order to restore their devices (and often this doesn’t happen, even if users pay up), a cryptojacking program hides in the shadows.
Only 2 weeks ago, researchers uncovered a new Monero mining malware program that hides from Windows’ Task Manager module.
Conversely, phishing schemes aim to trick and deceive unsuspecting users into revealing their private key or recovery seed online or over the phone. New Bitcoin and Litecoin threat crypto dusting (see our new crypto dusting security guide) “pollute” thousands of blockchain addresses with tiny amounts of crypto in order to ascertain the users behind big accounts so that they can try to phish or extort them.
Cryptojacking malware applications do not try and steal existing virtual assets. They’re only concerned with stealing your computer’s processing resources to produce new virtual assets.
Why is Cryptojacking increasing?
Cryptojacking is a more subtle way of stealing cryptocurrencies. While phishing and ransomware is a numbers game where users have to be tricked into or threatened to hand over their virtual assets, crypto-mining software just needs a simple click to secretly install in the background and start mining, with the user none the wiser.
It’s easier, less risky and more profitable for criminals to try and infect users’ computers with cryptojacking malware instead of ransomware like WannaCry that might attract a lot of attention from authorities and security experts because it can bring businesses to a standstill.
When did Cryptojacking Start?
According to this Wired report, “The Year Cryptojacking Ate the Web”, it became a real problem in 2018, in the aftermath of Bitcoin’s incredible bull run of late 2017, which pulled the altcoins like Monero up with it.
This Malwarebytes article pinpoints the origin of cryptojacking to September 2017, with the advent of the notorious CoinHive service. In 2017 cryptojacking attacks increased with 8500%.
By mid-2018, cryptojacking represented a staggering 35% of all web security threats.
The Role of CoinHive
Many crypto security experts point the finger of blame at a now-defunct mining service called CoinHive as the root of all cryptojacking evil.

CoinHive started off rather innocuously in late 2017 as a software tool that helped website owners to monetize their visitors. They did this via crypto-mining scripts that ran in the background and siphoned off some of their devices’ processing power while they perused the website. Many established sites like Salon and UNICEF publically used their services. However, there was a massive outcry when web users became aware that CoinHive exploited their computing power without consent.
CoinHive was finally pressured into shutting down in February 2019 by the falling prices of Bitcoin and Monero, improved ad-blocking browser extensions, better anti-virus software and the plummeting ROI from mining hardware.
Unfortunately, it didn’t take long for hackers and bad actors to open CoinHive’s Pandora box of cryptojacking know-how. They copied the CoinHive script and make a few tweaks before re-deploying it online for more unscrupulous and illicit purposes.
In 2018, Coinhive-related malware was found in Google Youtube ads and blamed for the massive MikroTik router attack in Brazil.
As a result, there is now a plethora of crypto-mining programs out there that affect consumers to nuclear plants and governments.
Who is behind cryptojacking malware?
While cryptojacking software can cost as little as $20 on the dark web, the sophistication and skill involved with cryptojacking vary greatly.
Reports indicate that government-sponsored North Korean hackers have stolen over $2 billion worldwide, especially from South Koreans, through cryptojacking and ransomware. Much of this money is of course once again plowed back into the North Korean war economy.
Crime syndicates and hacker groups are also behind much of the attacks. They then use the stolen crypto to fund anything from money laundering, criminal activities like human trafficking to terrorism.
Examples of Cryptojacking
While cryptojacking seems like a new security threat, it’s been around for a while, affecting companies like Tesla and even governments.
The methods and exploits used by hackers are becoming increasingly sophisticated. Here are a few examples:
In Brazil, multiple cryptojacking efforts lead to the infection of over 200,000 MikroTik routers that eventually spread to enormous amounts of web traffic globally.
MinerGate stops its operations when it detects mouse movements, so essentially, when a user starts to use his or her computer, the script goes silent so as to avoid detection.
Employees of big companies often use their companies significant processing power to mine crypto after hours. This can result in huge security vulnerabilities for the company.
P2P software such as BitTorrent variants also almost undoubtedly mine cryptocurrencies while you’re downloading your latest movies.
GitHub users should beware. Hackers often fork projects, then upload an infected version without the original developers’ knowledge.
CoinHive-like malware still roam the Internet, even spreading through YouTube ads last year.
BadShell uses windows processes such as Task Scheduler and Register to mine crypto in the background.
Certain software like CoinMiner actually searches out already-installed cryptojacking software, destroys and then replaces it.
How does Cryptojacking happen?
Cryptojackers can infect anything from websites, routers to Playstation 4’s and IoT devices. Often times, hackers use one of the following methods, or in many cases, both.
Cryptojacking by Phishing
Bad actors often catch their prey ( and their machines) by sending infected emails and other types of communication to users. While your email service provider should catch most of these bad emails, some might slip through the cracks.
Cryptojacking by Website or Ad Script
According to CSOOnline.com, hackers can also mine crypto by injecting a script into a website or a pop-up advertisement. When visitors click on the compromised site or ad, the script starts to mine and sends its proceeds to the hackers’ server.
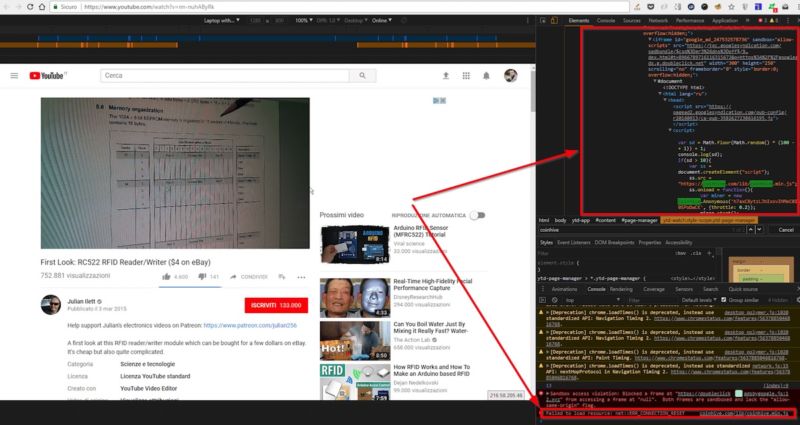
How can I prevent cryptojacking on my devices?
According to CsoOnline.com, users can utilize to fortify their computers and devices against cryptojacking as follows:
Company Security Training
If you’re a company, ensure that your employees are aware of the dangers of cryptojacking. There should be clear training that advises them to not open emails from unidentified senders or visit websites that trigger a security warning.
Anti-mining browser blockers
Most cryptojacking attempts come via website visits, so it’s important to make sure that your web browser has a strong crypto-mining blocker.
Some browser extensions like AdBlocker Plus has extra features that can be activated.
Chrome
Chrome users can download the MinerBlock extension.

Mozilla Firefox
Earlier this year, open-source browser Mozilla released a new version that specifically neutralizes crypto mining scripts. It’s called Firefox Quantum and the feature can be toggled on and off. Download it here.
Anti-virus software
Make sure you have a comprehensive and resilient anti-virus solution to guard your whole computer’s security.
How to detect if your computer’s been cryptojacked
Task Manager (Windows)
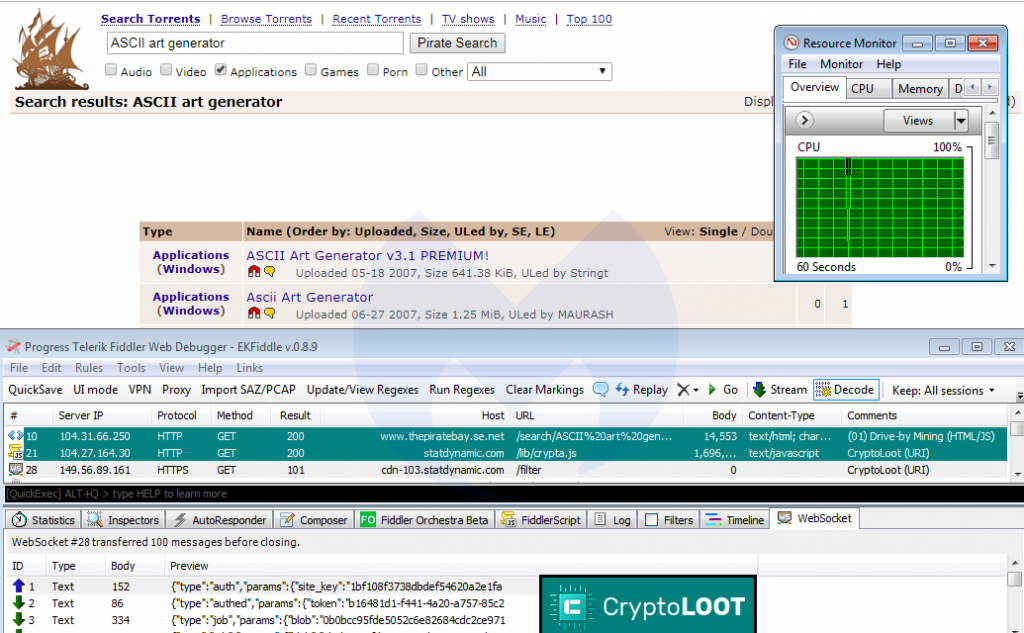
Usually, if your computer’s CPU starts maxing out at 100%, it’s likely that your device has been infected. You can monitor programs running for Windows via the Task Manager function. However, keep in mind, some new sophisticated crypto-mining tools shut down when you activate Task Manager, and then relaunches once you close the computer usage tracker.
Opera Tool
The Opera browser has a website that runs a free diagnostic tool to see if your device has been compromised. You can try it here https://cryptojackingtest.com/.
How to remove cryptojacking software
Removing cryptojacking really depends on a wide set of variables, such as type of script, individual or a company, sophistication level of the malware etc, and should be considered on a case-by-case basis.
Website owners
For WordPress site owners, you can check if your site’s been compromised with this tool.
Businesses
For consumers and businesses, it’s maybe a more sensible option to get professional security experts to help. This article explains more.
Consumers – How to remove BitcoinMiner Trojan
If you’d like to try and remove the BitcoinMiner Trojan malware by yourself, this step-by-step guide shows you how, at your own risk.
Overall, with cryptojacking and other cryptocurrency-related security threats, prevention is better than a cure. Make sure to apply best practice tips to stay safe.
NEXT TIME: We look into the big bad wolf of cryptocurrency threats: RANSOMWARE
Written by Werner Vermaak
Disclaimer: CoolBitX does not endorse and is not responsible for or liable for any content, accuracy, quality or other materials on this page. Readers should do their own research before taking any actions.
CoolBitX is not responsible, directly or indirectly, for any damage or loss caused by or in connection with the use of or reliance on any content, goods or services mentioned in this guide.







