You don’t need to be a security expert to protect your virtual assets like Bitcoin, just a quality hardware wallet and a healthy dose of common sense and discipline.
Who this article is for:
✓ Owners of a hardware wallet – a dedicated cold storage device for virtual assets that keeps your security data completely offline (as opposed to online and “hot”).
Why do you need a hardware wallet?
The only way to keep your private information truly safe is to
✓ control it yourself ( unlike centralized exchanges)
✓ keep it completely offline at all times (unlike Internet-connected software wallets)
✓ Make sure its physical form has extra security measures (unlike a paper wallet)

You’ve got a hardware wallet? Congratulations. So…
1) you’ve taken the plunge to invest in cryptocurrencies such as Bitcoin, AND you’ve gone one step beyond and decided that:
2) you’re giving your crypto runners the best shot at survival by keeping them on a hardware wallet, hopefully, the CoolWallet S.
Now it’s time to kick back and watch your investment grow. Job done, right?

Unfortunately not. With Bitcoin prices soaring, Crypto Summer is officially back, and with it, predictably, scammers.
Today, we’ll look at the essential checklist you have to follow to make sure that you get the best out of your cold storage device.
Please note: For the purposes of this article, we’re only looking at cold storage device security.
Software wallets like MyEtherWallet (MEW) , Electrum and Exodus bring a slew of different phishing and hacking problems that we discussed in another article.
What type of hardware wallets are there?
Hardware wallets either look and work like USB devices (for computers) or a smart card that communicates with your mobile phone via encrypted and secure Bluetooth. In 2019 we’re also starting to see hybrid USB devices with Bluetooth capability.
Very important, is whether your hardware wallet has a CC EAL5+ Secure Element to protect the private keys and sign transactions.
The industry leaders are:
- Bluetooth: CoolWallet S, ( first mobile hardware wallet in 2016, with Secure Element)
- USB: Ledger Nano S (market leader, with Secure Element)
- USB: Trezor Model T (first hardware wallet in 2011, no secure element)
- USB/ Bluetooth: Ledger Nano X ( first hybrid in 2019, still suffering bugs)
3 Ways to lose your crypto quickly
Did you think owning a hardware wallet meant you’d never have to worry about losing your virtual assets again?
Wrong.
Doing any of the following may result in you losing your virtual assets.
❌Revealing your private keys
❌Revealing your seed recovery phrase
❌Losing your paper wallet (recovery seed)
While cryptocurrency hackers are often extremely resourceful, the sad truth is that in almost all cases, crypto losses suffered via hardware wallets are the result of the owner’s negligence, not a device defect.
Now, repeat after me:
☠ Rule 1: NEVER Reveal your Private Keys to Anyone
Good News: If you own a Coolwallet or Ledger with a Secure Element, there’s no need to fret about keeping your private keys safe. Your most sensitive information is forever safely ensconced within the Secure Element and in almost all cases, cannot be extracted by any party, not even us.
CoolWallet and Ledger hardware wallets come with cutting-edge Secure Elements with the highest external certification (CC EAL 5+).
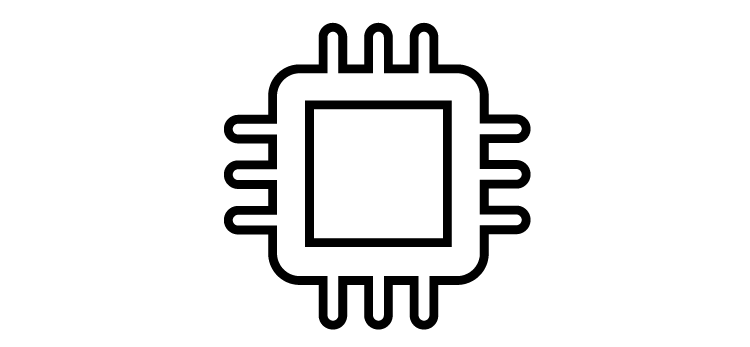
A Secure Element (SE) (CC EAL5+certified) is like Fort Knox for private keys and the best precaution you can take. It’s a microprocessor chip that stores sensitive data and acts as a vault. It’s virtually impenetrable and protects the private key at all times and makes sure it is never revealed to ANYONE, not even you or us!
If your hardware wallet doesn’t have a Secure Element, it might have other innovative but less secure ways to safeguard your private key, like Trezor does.
☠ Rule 2: Never Reveal your Recovery Seed Phrase to Anyone!
That leaves only your Recovery Seed Phrase, a paper wallet that contains your written seed words or numbers, as the quick and easy way to steal your funds and boy, these scammers are going all out in their efforts.

The First Rule of Recovery Seeds is…
There is no recovery seed. Well, it exists and is hidden somewhere only you know. Where possible, keep as few creatures informed about the fact that you own a hardware wallet as possible. That includes your dog and goldfish. Who knows who’s listening?

Remember, 50% of marriages eventually end and some family feuds are never resolved. Also, your dog can’t even guard your home, and will likely eat your paper wallet.
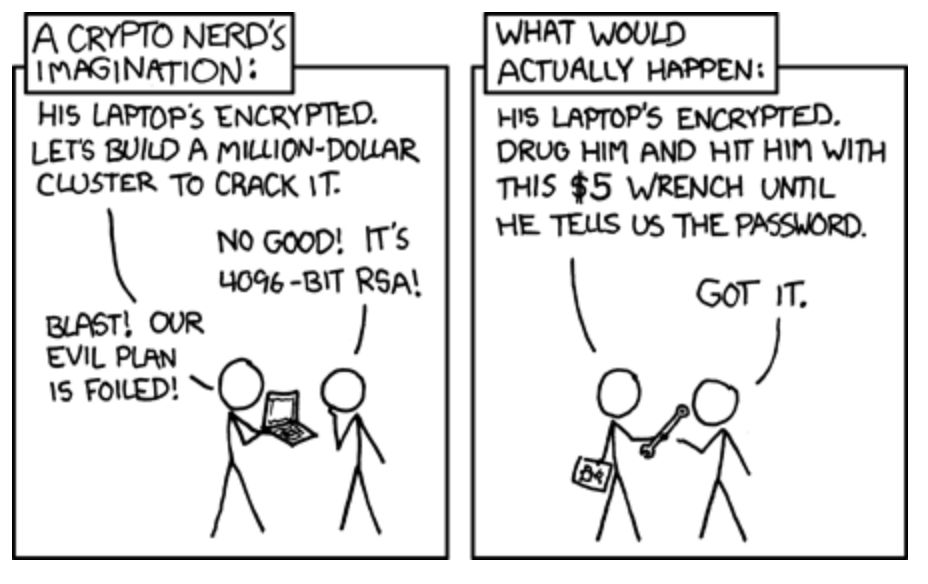
But seriously, talking about your virtual assets puts you at risk of what Trezor calls the “$5 wrench attack”, where someone can physically force you to reveal your recovery seed through violence. About 3 in 5 Hollywood movies get made based on that plot twist, so what makes you different?
Don’t Be A Phish!
In poker parlance, a “fish” is a player who is inexperienced and easily loses his money. He or she is essentially a sucker, there to be exploited. Not much is different when it comes to cryptocurrency and the art of phishing.
As an Internet user, you might come across a phishing attempt in the following ways :

1. Phishing Malware
Clicking on the wrong link can have devastating results, either directing you to a fake website, which will then manipulate you into entering your secret phrase or installing hidden spyware, such as keyloggers, that will allow them to intercept your private information next time you enter it.
2. Phishing by Impersonation
There are currently tens of thousands of scammers impersonating well-known crypto personalities and companies on any possible platform, from Twitter to customer phone service lines.
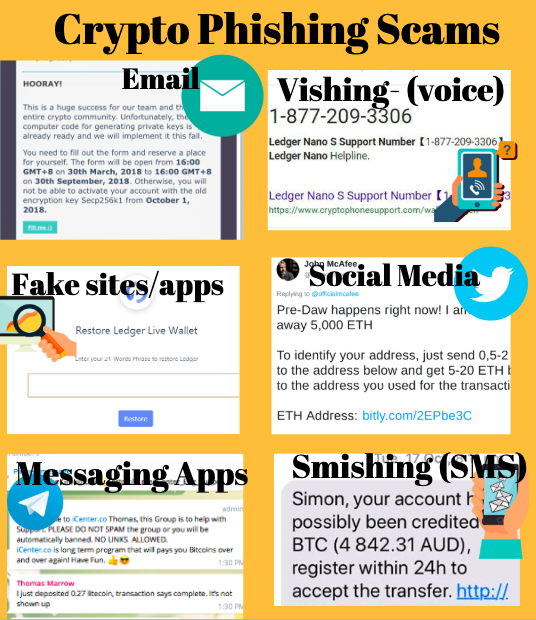
Scammers are especially active on Twitter, often replying to authenticate tweets from crypto influencers or exchanges, by picking the same title, but with a similar-sounding user ID. For example:
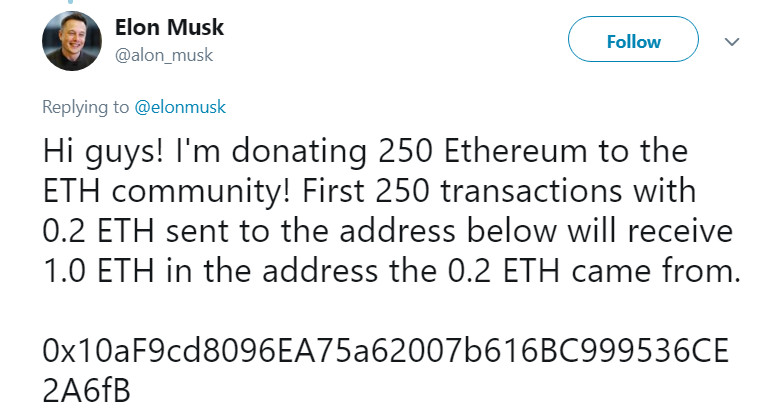
Not so fast, “Alon Musk”. Yet, these fake posts are getting smarter, often disguised as a comment in a Twitter thread, and worst of all they still WORK.
Why?
Because cheating someone out of their crypto is a numbers game.
While 9999 out of 10,000 users dismiss a scam post by now almost instinctively, there is, unfortunately, always that one exception to the rule. That one person who is new to virtual assets, dreams of getting rich and unsuspectingly sends 0.05 BTC in the hopes of receiving 1 BTC or more back, makes it worth the scammer’s time to do this, time and time again.
It’s 2019. Don’t be a phish who falls for 2017 tricks. 🎣
Rule 3: Don’t Lose Your Hardware Wallet Seed
By now you should know to never reveal your recovery seed or private key to third parties under any circumstances. However, even more important is to make sure that the physical paper wallet seed is CORRECT and KEPT SAFE at all times.

Don’t try to only memorize it, or keep different sections of it in different locations, or play clever games with it. Accidents (and alcohol) happen. Keep it in a secure and dry place, like a safe or a steel wallet.
5 Tips to Protect Your Recovery Seed
1. Generate your hardware wallet seed in private
That means alone. Private. Solo. Don’t ask that tech bro in your office, your handy brother in law or even customer support to help you set up your wallet. Trust no one!
2. WRITE DOWN your recovery seed on a paper wallet
Always write down the seed backup from your hardware wallet’s screen.
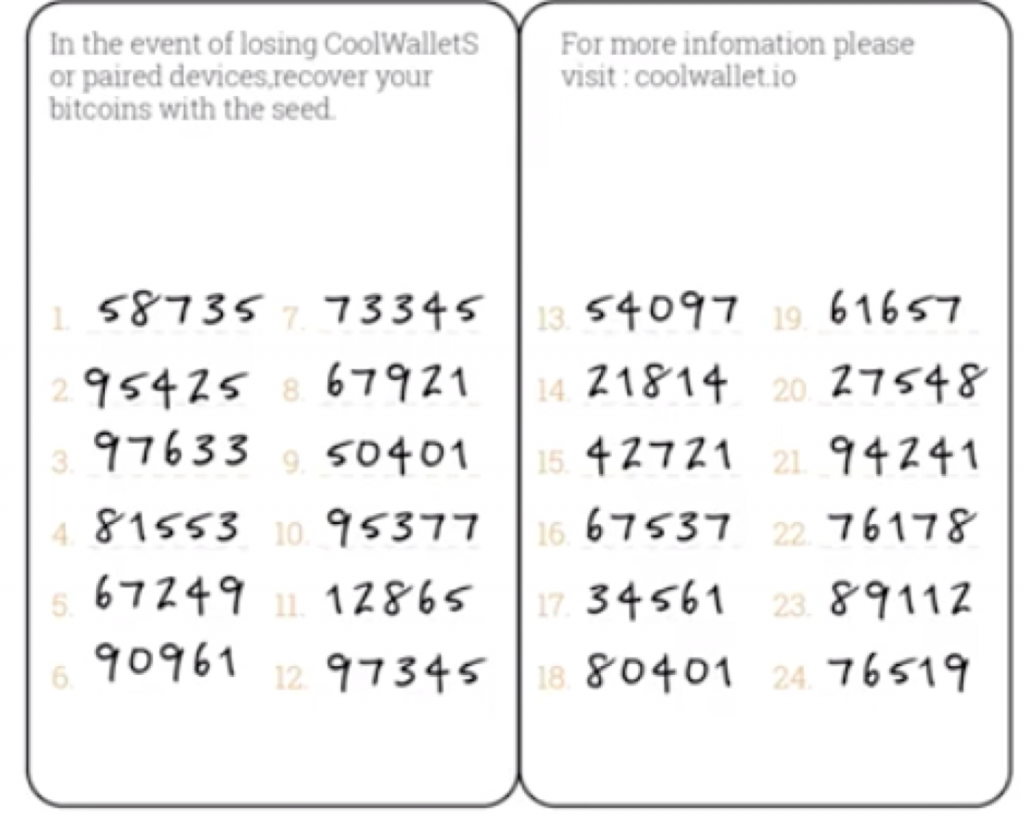
3. Double-check that you’ve written it correctly, in the right order.
You can learn more about how seed phrases and numbers are generated here. Basically, they are derived from words in the dictionary and there’s theoretically up to 2^32 different options, based on the order of each seed set. So, take a couple of minutes and go over once more. Or you might spend the rest of your life trying to do it after the fact.
4. Never print, take a photo or store a digital copy of your recovery seed
Photographing, printing or saving a copy of your private key or recovery wallet is just plain lazy. It also creates a digital copy that can be exposed. Digitize your seed, and potentially vaporize your holdings.
5. Never type your hardware wallet’s recovery seed
Your device may not be secure. If you don’t know why, scroll back up and read Rule 2’s section on phishing again.
Final Thoughts
It is extremely unlikely but possible that a private key can be extracted from a cold wallet if a hacker gains physical access to both your device and connected phone/ computer at the same time.
Some hardware wallets can be cracked by installing physical components into the USB device or intercepting and decoding transmission signals.
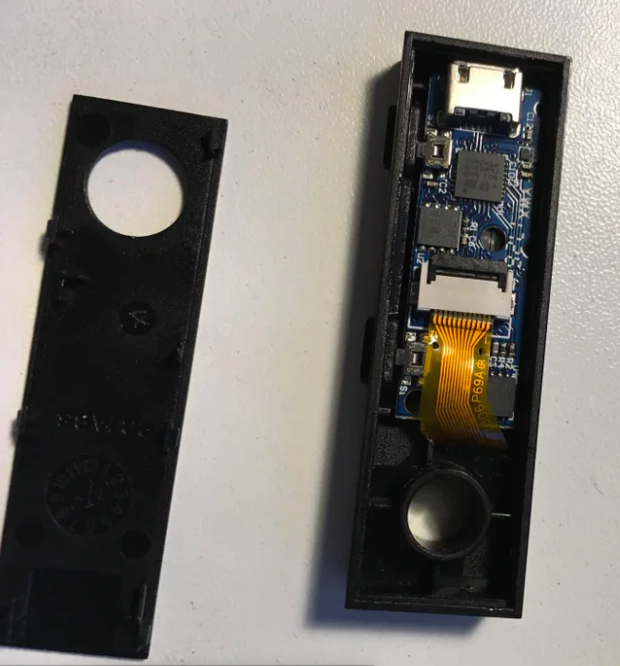
It’s extremely unlikely and complicated though. A Secure Element prevents that, by denying access to your private keys at all times. (see Ledger’s Secure Element guide).
Owning a hardware wallet is a conscious assertion that you are 100% invested in the future of your cryptocurrency assets for the long haul and believe that they will one day have great value.
By exercising caution and the measures above, you should ensure that your virtual assets stay ice-cold under pressure at all times.
Unless quantum computers or something. But that’s a story for another day. Just kidding!