Last week, leading hardware wallet company Ledger created a media frenzy with a damning security report that criticized the security of their competitor Trezor’s products.
Unsurprisingly, Trezor released its own statement soon after that rubbished Ledger’s claims and questioned the French company’s intentions.
Ledger itself has suffered quite a few serious security issues over the years, so is this a case of the pot calling the kettle black, or is there something more to this story?
As the makers of the CoolWallet S, the world’s best Bluetooth hardware wallet for everyday use, we’ll try to objectively review both Ledger and Trezor’s claims and pick a “winner”, even though we think this is essentially a lose-lose situation for both companies.
To do this, we’ll take a look at crypto protocol and also give a bit of backstory to this simmering rivalry by seeing how 2018’s seismic Wallet.Fail ethical hack demo fits into all of this.
We’ll answer these questions:
- Was Ledger within their rights to “badmouth” Trezor and did they follow the correct protocol?
- Should crypto companies expose each other, even if this risks damaging themselves and the industry?
- What security issues did Ledger find with the Trezor, and are they really credible vulnerabilities?
- Which is more important – protection against remote attacks or physical attacks?
- What is a Secure Element, and does my hardware wallet need it?
And if you must know, we take no satisfaction in the fact that two of our biggest competitors are going after each other.
We’re just here to watch!
Crypto Protocol: Does it even exist?
All jokes aside though, with the crypto industry is still in its absolute infancy, virtual currency companies are still forced to learn and fix holes by trial and error and benefit greatly from outsider perspectives. In many cases, competitors are often forced to pool resources together or share information in order to collectively grow the category together.
Crypto hardware wallets: A brief history
Cryptocurrency hardware wallets are essentially offline vaults that safely store users’ private keys. This industry is still very young.
Trezor is a true pioneer in crypto, having brought out the first cold storage wallet in 2011.
Three years later, 2014 saw both Ledger and CoolBitX, maker of the CoolWallet S take their humble first steps.
Ledger and Trezor devices connect to your personal computer via USB, which makes them vulnerable to tampering and hacking.

CoolWallet S, on the other hand, was the first Bluetooth hardware wallet and looks like a credit card, making it impossible to open.
In 2019, Ledger also finally released a Bluetooth hardware device, albeit still a USB device.
The crown jewel in both the CoolWallet S and Ledger range is a sophisticated Secure Element (SE) that protects the user’s private information and stops unauthorized transactions.
Responsible Disclosure & Bug Bounties
Cold storage wallets use incredibly complex hardware and software that require constant updates and testing to keep it in step with third-party cryptocurrency projects and ahead of hackers and scammers.
As a result, companies rely heavily on external testing from the community to identify security vulnerabilities. They reward users who find bugs with bounties, much the same way video game developers do with players who report bugs.
As with other tech products, any potential weaknesses that are identified and fixed before they get exploited are useful to the entire industry as this improves overall security and therefore more trust in cryptocurrencies in general.
For example, Ethereum’s Constantinople hard fork was delayed in January with only a few hours to spare, after a digital security consultancy found a catastrophic flaw in one of their improvement protocols, which had the potential of resulting in millions of dollars of lost crypto.

Successful bounty programs like those of Ledger and Binance usually require ethical hackers (hackers who penetrate a device’s security in order to help improve it) to first contact the company directly and present their findings to their technical team, who will verify the security issue and after a lengthy process, issue the relevant rewards.
This process gives the company a chance to get their house in order before they publicly release their response.
Of course, in an industry created by smart people who don’t like to follow rules, this is not always the case.
Wallet.Fail Demo (2018) Hacks Ledger and Trezor
In late 2018, three high-level security experts conducted a press conference which sent shockwaves through the whole virtual currency industry.
Over the course of an hour, the Wallet.Fail presentation, lead by respected security researchers Dmitry Nedospasov, Josh Datko and systems engineer Thomas Roth, exposed major security holes in the Ledger S, Ledger Blue and Trezor hardware wallets, as follows:
Ledger Nano S:
The team installed a hardware component on this device, which with the use of spyware, allowed them to extract the wallet’s PIN. They also installed custom firmware to get partial access to the Ledger S and claim they were able to show false and send malicious transactions.
Ledger Blue:
The Wallet.fail trio intercepted radio signals used by the device and stole the wallet’s PIN.
Trezor One:
The team managed to flash the hardware wallet with customized firmware in order to successfully obtain private keys and access wallet funds.
Trezor’s CTO was actually at the event and gracefully extended an invitation to work with the Wallet.Fail team in the future. We also have to note that the hackers praised Trezor’s impenetrable firmware, but insisted that its lack of a secure chip is a big safety risk (watch from 54:00).

Both Ledger and Trezor gave a muted response following the demo, claiming that the Wallet.Fail team hadn’t followed “Responsible Disclosure” protocol and that the issues highlighted were either already resolved or plainly impractical. You can read Ledger’s reply here.
While this public dressing-down might’ve been tough to swallow for Ledger and Trezor (well at least their PR departments), who pride themselves on providing virtually hacker-proof cold storage, it’s also good for them and other hardware wallet makers in the long run.
The companies reap the huge rewards of having their products objectively reviewed and battle-tested by some of the industry’s best.
But next time, hopefully not quite so publicly.
Crypto Competitors: Guilty By Association?
The overarching wisdom in the world of cryptocurrency is that whatever’s the greater good for the industry should determine what’s best for a company.
However, there is an unspoken rule between crypto companies that they will not directly attack each other.
The reason is simple:
In the crypto-industry, your company can quickly become guilty by association if you highlight a competitor’s weaknesses or problems that you might inherit tomorrow.
Moreover, it could be misconstrued as pettiness (see Ethereum’s Vitalik Buterin badmouthing Tron and Justin Sun) and it could alienate users.
Ledger’s Security Report on Trezor
On 11 March 2019, Ledger posted a rather pious-sounding article on their blog, with the following title: “Our Shared Security: Responsibly Disclosing Competitor Vulnerabilities”.
“We have a responsibility to enhance security throughout the entire blockchain ecosystem whenever possible”
Ledger claimed that as the “global leader in blockchain solutions”:
“We have a shared responsibility in guaranteeing a high level of security for the entire industry.”
Ledger Report
What is the Ledger Donjon?
Ledger has an expert in-house security team that tests and exposes security flaws on both their own and competitor hardware wallets. The team has the catchy name “Ledger Donjon” and is comprised of 8 highly experienced security experts who assess both internal and external security threats.

Apparently in late 2018, their hacking team moved their attention to Trezor, and identified massive security issues with their Trezor One and clones Trezor wallets.
Ledger claims they will inform any competitor or third party of their results first before they make it public.
They shared their findings with Trezor 4 months ago (a month before the Wallet.Fail scandal broke). Since the responsible disclosure period had now come to an end, they were within their rights to release their findings to the public.
Quite benevolent of them, right?
Not so fast.
Trezor responded with their own statement a few days later, blasting the Ledger report as inaccurate, insincere and overblown.
Ledger Report: Overview
What is a “Supply Chain Attack”?
A supply chain attack happens when a hacker modifies the behavior of your cryptocurrency device by secretly intercepting it or infiltrating your network or software through an exploited weakness they found in a third party’s security.
For hardware wallets, this normally implies a physical attack on the device, where a hacker intercepts your device en route to the customer, opens it and installs a malicious component. When the customer receives the hardware wallet and sets up the wallet seed, this information is compromised and revealed to the attacker.
It’s a very big security issue for USB-form hardware wallets like Ledger and Trezor, which can easily be opened and resealed before it reaches unsuspecting customers.
However, Ledger officially considers this a benefit that allows their users to inspect the device internally to make sure it hasn’t been tampered with.
1st Vulnerability: Supply Chain Attack – Device authenticity
Ledger also succeeded in opening the Trezor, installing a malicious backdoor and then re-sealing it once again, even reapplying the tamper-proof sticker.
Claim: The Trezor can be cloned
Ledger claims in their report that the “genuineness of Trezor hardware wallets can be imitated”. This is worrisome. Ledger was able to manufacture exact clones that were virtually identical to the real thing, with the same components and look and feel.
Claim: The Trezor can be opened and tampered with
Both the Ledger and Trezor can be opened and their circuit boards offer enough free space for malicious components to be installed.
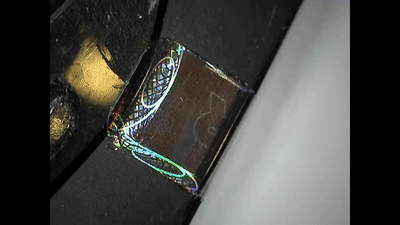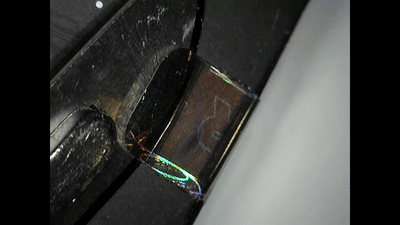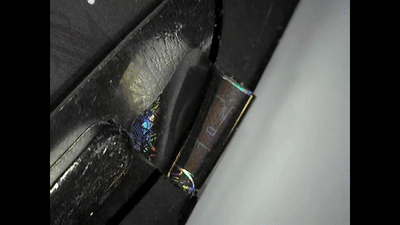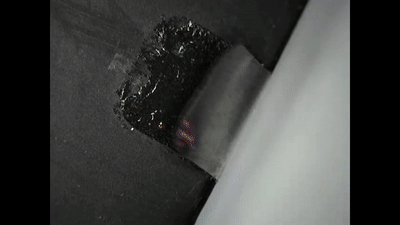
Once compromised, a backdoor exploit in a hardware wallet like Trezor and Ledger can result in a pre-seeded device or malware that sends transacted funds to different addresses or extracts the seed.
Ledger rightly points out that even if you purchase your Trezor directly from the manufacturer, you’re still not guaranteed that the device you receive is the real deal. Attackers could buy devices, modify them, then return the item as part of their money-back guarantee.
Then again, the same applies to Ledger devices.

This is one of the biggest reasons that CoolBitX decided to create a hardware wallet card. The CoolWallet S is essentially tamper-proof, thanks to its wafer-thin slimness and compression technology that makes any physical breaching attempt immediate visible to the naked eye.

Fun Fact:
Did you know Ledger brought out a NFC “smart card” wallet but discontinued it due to technical issues? It was called the Ledger Unplugged. This makes the CoolWallet S even more impressive!

Ledger’s Solution – a Secure Element
Ledger then says that they reported this issue to Trezor, and that it is such a fundamental flaw that the only fix is to redesign the Trezor One and add a Secure Element, instead of a general purpose chip they currently use.
What is a Secure Element?
A Secure Element (SE) is a microchip inside a security device that protects its private data from being stolen. It acts as a vault and is an impenetrable final layer of defense against attackers.
You can learn more about the importance of secure elements from Ledger’s CEO himself here.
Secure elements are certified by third parties who test it according to a list of requirements known as Common Criteria (CC).

Both the CoolWallet S and the Ledger product range have Secure Elements that carry the industry’s highest security approval, namely CC EAL5+.
Vulnerability 2: Side-Channel Attack – Insecure PIN
Without going into too much technical detail, Ledger claims that it is possible to guess a Trezor user’s PIN via a side-channel attack.
What is a Side-Channel Attack?
A side-channel attack is where an attacker intercepts sounds, frequencies, timings and power consumption emitted from internal electric circuitry and analyzes it to decipher concealed private information.
Ledger claims an external device can measure the power consumption of PIN attempts and figure out the secret code by comparing it with that of a valid PIN login.
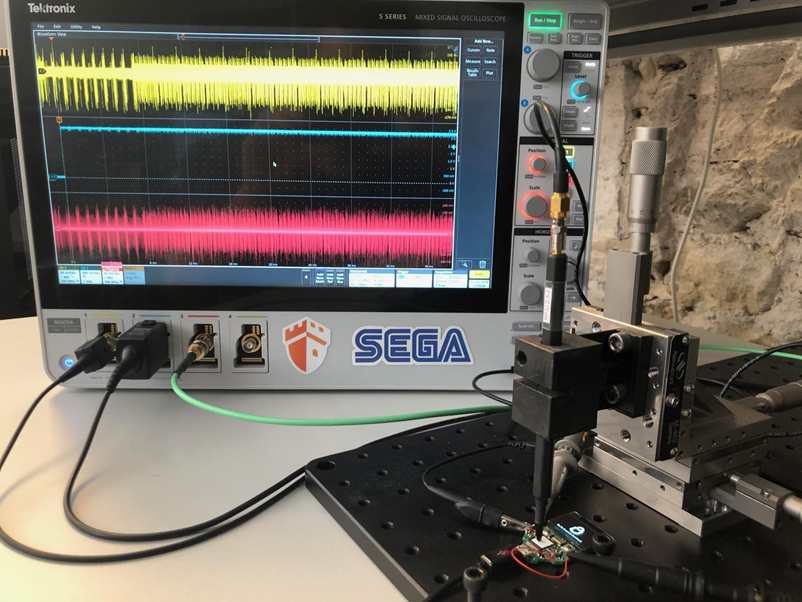
Ledger does mention that they reported this issue to Trezor on 20 November 2018, and it was subsequently patched.
Strangely though, only one month later Wallet.Fail did a similar exploit on the Ledger Blue. Ledger called the attack “interesting” but unlikely in real life, as a device would have to be the same position and controlled environment each time.
Which is exactly what they did to the Trezor in the picture!
Vulnerability 3 and 4: Internal data confidentiality
Ledgers’ report states that a hacker who is able to physically access the device, can extract private information from the Trezor One and T’s flash memory. Again, it can only be fixed by installing a Secure Element chip inside the Trezor. Ledger does concede that this security issue can be circumvented via a strong passphrase.
Vulnerability 5: Cryptographic Stack Analysis (side- channel attack)
Ledger found that someone with physical access to Trezor can extract the private key via a side-channel attack that targets Scalar Multiplication, one of cryptography’s most important functions.
An attacker needs to know the PIN beforehand, then use a digital oscilloscope to “listen” to the private key. This vulnerability can be patched but isn’t as of yet. Ledger thereby disputes Trezor’s claim that it is secure against side-channel attacks.
End Result:

Trezor’s Response: “Nothing exploitable remotely”

Trezor swiftly responded with a long rebuttal on Medium. It was clear that Ledger had struck a nerve. Trezor strongly stated that none of the vulnerabilities Ledger found was exploitable remotely, and required an attacker to be in possession or close proximity of the hardware wallet.
The “$5 wrench attack”
The cold storage company mentioned that in any case, no physical hardware wallet security is immune to a simple “$5 wrench attack”, a targeted theft where an attacker can just get the private information for a hardware wallet owner by violent means.
This pretty much means that if someone can get close enough to you to either get physical control or access to your hardware wallet, then it’s much more likely that they will most likely follow an easier, more direct option than the theoretical ones highlighted by Ledger.
Trezor says their main focus is on protecting their product against remote attacks, not physical attacks.
Here is Trezor’s summarized reply:
- Supply Chain Attack: Out-of-scope, affects all hardware in transport, no 100% solution, all companies have different methods to mitigate this
- Software Crappy Attack: Non-exploitable, patched
- Side Channel PIN Attack: Patched
- Side Channel Attack Scalar Multiplication: Non-exploitable, PIN required
- Surprise Concluding Attack: Not fully disclosed, implications for all hardware devices based on ST microchips, mitigated by a passphrase

DELIVERED EVERY WEEK
Subscribe to our Top Crypto News weekly newsletter
Trezor ultimately concludes that all hardware is vulnerable, but that each company can use tools to lessen the danger of certain threats.
Trezor considers their passphrase feature as their primary defense tool against what they consider to be the most severe security vulnerability: remote attacks.
Industry reaction – Ledger’s “Trojan Horse”?
To complicate matters furthers, crypto publication Crypto Briefing posted a series of tweets on March 12th, where they alleged that they’ve been contacted by Ledger’s PR firm to place a story about the Trezor report.
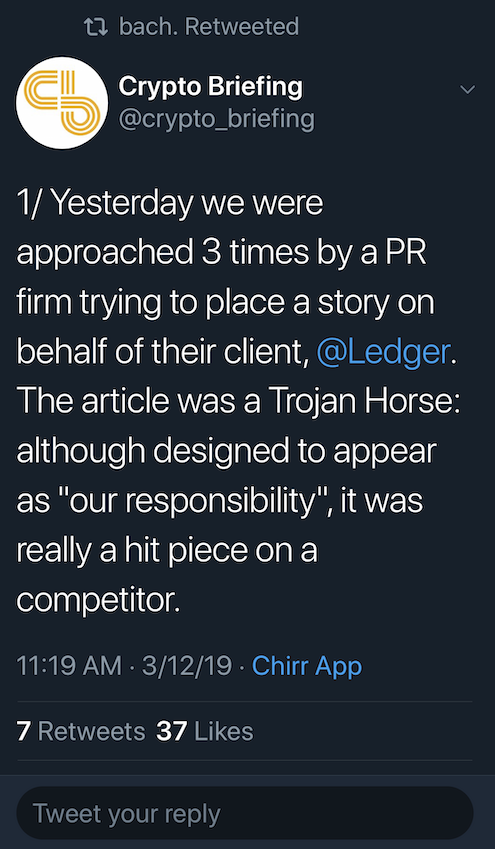
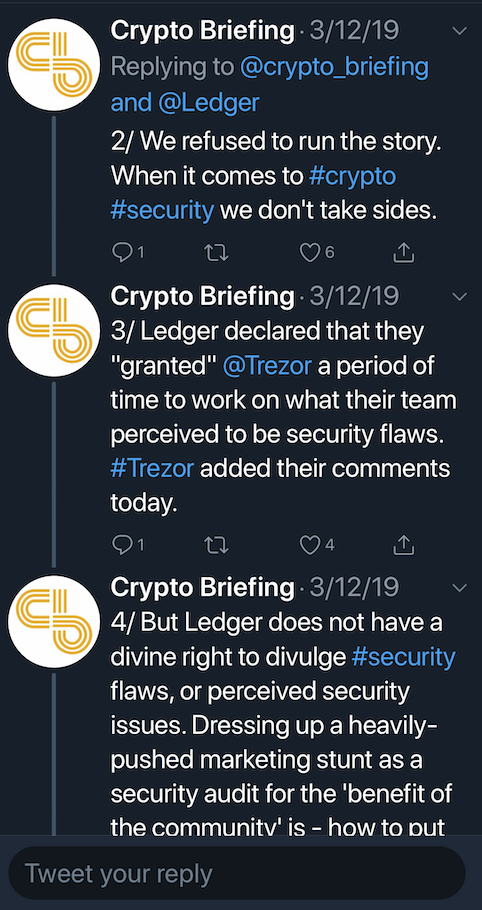
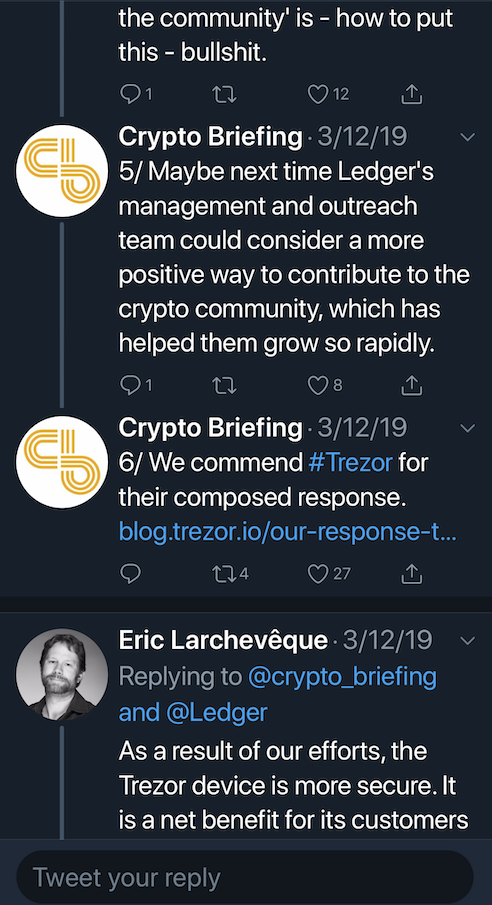
They refused, claiming it was a “Trojan Horse”, a hit piece disguised as social responsibility. This certainly raises more than a few questions.
The Case For/Against Ledger & Trezor
There are a few obvious reasons I can think of why Ledger could’ve decided to attack Trezor.
These are:
- Ledger wanted to damage Trezor’s credibility and diminish them as a competitor.
- They simply wished to responsibly disclose vulnerabilities they found, in accordance with their social responsibility policy.
- Ledger needed to publicly create some distance between them and Trezor as a result of the Wallet.Fail demo or because they want to be able to say “we told you so” when Trezor inevitably gets hacked.
The Case For Ledger
Of these 3 scenarios, I personally think that all three reasons are in play here.
An unspoken rule in business is that the market leader often publicly ignores Number 2, unless they pose a serious threat. As the market leader, you are expected to lead by example and not give unnecessary attention to competitors, even if negative, as it makes you look weak.
In return, competitors have a green light to attack the market leader.
Examples include Hertz and Avis (“We try harder”) Mercedes vs BMW and the UFC vs Bellator.
Therefore, Ledger would probably not risk their reputation or come across as petty if they didn’t believe users’ funds were legitimately at risk.
The Case Against Ledger
However, CryptoBriefing’s accusation leaves some serious questions as to Ledger’s sincerity, and whether this indeed was a hit job on a respected competitor.
It is also possible that the Wallet.Fail expose left a festering wound that Ledger feels needs treating. The demonstration basically lumped Ledger and Trezor together as non-secure hardware wallets, and this might be Ledger’s way of trying to separate themselves from Trezor and restore their reputation as security experts.
Finally, there’s also the sad matter of the crypto winter that has put the whole industry in a stranglehold since 2018. In an increasingly competitive market with diminishing returns and margins, it might be a case of Eat or Be Eaten.
The Case for Trezor
As the first cryptocurrency hardware wallet and with its founding members very respected in the crypto industry, Trezor, of course, has a right to be upset and to decrypt Ledger’s report as a personal attack full of venom, hypocrisy and virtue signaling.
Some of the vulnerabilities Ledger go over in their report are actually ones that Wallet.Fail exposed in Ledger products.
Moreover, Trezor was surprised that Ledger mentioned the Sudden Concluding Attack vulnerability, as apparently, Ledger asked Trezor to keep this a secret earlier.
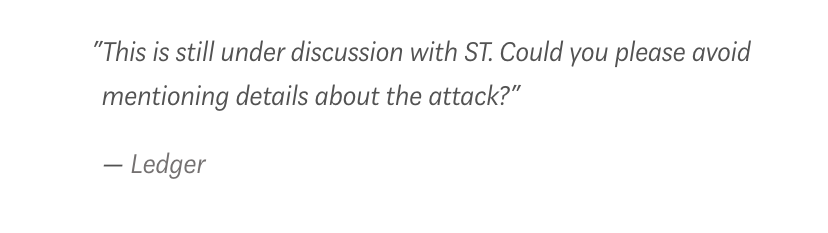
This is apparently a security issue that possibly affects microchips used in many other industries and could scupper negotiations with ST, a microchip manufacturer.
The Case Against Trezor
While Trezor does have an excellent security team and firmware, their continuing disregard for physical attacks on their devices is worrisome
Their argument is a bit flippant when you consider that many users could be stowing away a big chunk of their life savings or investment portfolio on their Trezor. Any proven deterrent such as a secure element will do a lot to dispel hackers and stop them before they even start their attack.
Of course, remote attacks are a massive threat. But a secure element also helps to protects a hardware wallet against that by signing only valid transactions.
Trezor’s dismissal of Ledger’s findings is tantamount to Apple or Samsung suddenly saying that their phones won’t require any biometric or PIN to be unlocked, as any criminal could just coerce a user by force to give up their private information through violence.
The Verdict- Ledger Vs Trezor

With such a complex mixture of social responsibility, technical considerations and loyal users to digest, it’s safest to say that both parties are right and wrong on some counts. Let’s look at what we can take away from this public spat though.
Is Trezor vulnerable?
No. Maybe?
Both sides present a compelling argument, depending on which way you look at it.
Trezor focuses on remote attacks which they consider to be a more practical threat and appears to be safe as long as you keep physical control over this hardware device.
While any hardware wallet can be vulnerable under some conditions, CoolWallet considers it of paramount importance to make it any physical hacking attempt so difficult that hackers in most cases don’t even attempt it. Stick with exchanges guys, please.
Secure Element – Prevention is always better than cure
There is just no good reason why a sophisticated device such as a hardware wallet should not go the extra mile and feature a Secure Element.
As long as your seed phrase is safely backed up, a secure element is your best final line of defense. It ensures that your private key NEVER leaves your hardware wallet, even if your phone or software is compromised.

The CoolWallet S also requires 2+1 Factor Authentication, which includes biometric verification on the app as well as physical confirmation on our hardware wallet to ensure that users don’t make any mistakes when transacting.
Should crypto companies name and shame each other?
Yes. An unequivocal yes, when it’s justified, respectful and procedures are followed.
Too long have crypto companies avoided drawing negative attention to the industry and themselves by biting their lip when they see malicious actors or blatant flaws in competitor offerings.
As a result, the crypto industry has seen over a billion dollars stolen in 2018, and 2019’s no different.
In an industry where a CEO can die and take 250 million USD “with him” to the grave (as recently happened with Quadriga), we need more whistleblowers and observers who are willing to do the right thing in order to help clear the path to mass adoption.
By following Responsible Disclosure guidelines and giving the targeted company enough time to investigate your claims and fix any issues before you go public, you also help to mitigate the fallout that might come from such a disclosure.
Because by now we know:
A blockchain and cryptocurrency solution is ultimately only as strong as its biggest weakness.

Till next week crypto family!
Disclaimer: This is an opinion piece that does not officially reflect CoolBitX or CoolWallet’s viewpoint. CoolBitX does not endorse and is not responsible for or liable for any content, accuracy, quality, advertising, products or other materials on this page. Readers should do their own research before taking any actions. CoolBitX is not responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in the post.