
A nasty new malware has been discovered that can empty your crypto wallet by stealing your private data via a Telegram bot and secretly modifying recipient wallet addresses. The Masad Stealer spyware disguises itself as popular software and cheats for applications like Fortnite and Binance. It is currently widely advertised and shared across the Internet by hackers who bought it on the Darknet.
Table of Contents
- Introduction
- What is Masad Stealer and Clipper?
- How does Masad infect computers and phones?
- What applications does Masad pretend to be?
- Who is behind the Masad trojan spyware?
- How Masad steals information and “clips” wallet addresses
- Which cryptocurrencies does Masad target?
- How to remove Masad Stealer spyware
Introduction
The Masad Stealer spyware targets computer and mobile phone users who access crypto or store sensitive information on their devices.
In this article, we’ll look at what the Masad Stealer is, who’s behind it, how it steals data and crypto, what data and programs are affected, and how to potentially remove it.
Masad poses the biggest risk to crypto owners who use their computers or phones to store private data or to send digital assets from their desktop wallets or digital exchanges.
This latest Trojan phishing scam is just another reason to keep your digital assets securely offline in a hardware wallet like CoolWallet S, that requires a physical confirmation check before any digital asset is authorized.
What is the Masad “Clipper and Stealer” malware?
The Masad “Clipper and Stealer” malware is a Trojan spyware threat that uses a Telegram Command and Control (C2) bot to 1) collect and exfiltrate (withdraw) sensitive data to anonymous hacker-owned Telegram accounts and 2) automatically “clip” and replace any crypto address you might copy in order to send funds to. It is likely based on the older Qulab Stealer malware.
The spyware passes itself off as popular tools and bundled third-party software that unsuspecting victims download and install. Worst of all, it’s being sold on the Darknet and currently already implemented online by multiple malicious groups and campaigns. This latest threat follows hot on the heels of new exploits Google’s Threat Analysis Group found on compromised iOS devices earlier this year.
How does Masad infect computers and phones?
The malware targets Windows and Android users, but it’s likely that iOS customers will also be affected soon. The developers of Masad were sly enough to cloak the malicious spyware as popular applications that users are likely to click on, such as hacks and cheats for games like Fortnite and Dota.
Researchers at Juniper Threat Labs have found that the Masad spyware infiltrates victims’ devices by posing as an authentic program bundled software or game cracks and cheats. The cloaked malware variants are widely promoted on the Internet and disseminated on web forums and file-sharing sites.
What applications does Masad pretend to be?
Just like the recently uncovered Syrk ransomware (see our guide), Masad can pose as a Fortnite aimbot. However, it also comes in a growing list of fake disguises that includes:
- Samsung mobile phone updates
- A Binance Trade bot
- CCleaner file removal program
- Hacked game cracks and cheats (PUBG/DoTA/Fortnite/GTA)
- For a full list, click here
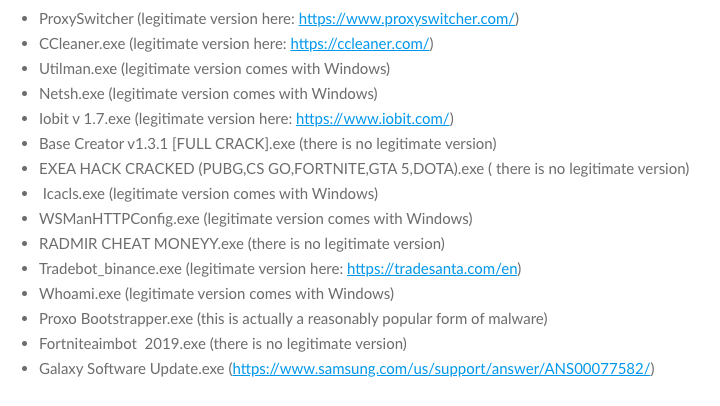
All the counterfeit files are executables (.exe) and some have the ability to then download and install additional cryptojacking malware upon their own installation.
Who is behind the Masad Stealer spyware?
The malware is brazenly being sold on the Darknet as freeware that increases in pricing, up to $85, as additional features get added. Incredibly, the criminals behind Masad have even set up a website and a private Telegram group that has around 300 members and likely offers technical support.

This means that there are now not just a few clever hackers behind Masad. With each copy of Masad sold, its network of bad actors grows. At present, over 300 Telegram bot IDs have been uncovered by researchers, coming from different attack vector distribution sources, and this could only be the start. Juniper estimates that over 18 threat actors or active campaigns currently involved in distributing the malware.
What happens after Masad infects a computer or phone?
The Masad malware program does what its full name suggests: It steals and it clips. Here’s what and how:
Stealing process
Step 1: Search for private data
Once it infects a device, such as a computer or phone, the Masad Stealer malware searches for any valuable data from its host device’s browser history and elsewhere. This includes:
- Cryptocurrency Wallets
- PC and system information
- Credit card and password data (browser)
- Installed software and processes
- Desktop Files or screenshot
- Browser cookies
- Steam authenticator files
- AutoFill browser fields
- Discord and Telegram data
- FileZilla files
(source: Juniper Research)
Step 2: Zip data and exfiltrate it via Telegram C2 bot
Next, Masad Stealer zips all the potentially damaging information it has extracted into a 7Zip file (the program is integrated into the malware binary) and then exfiltrates (withdraws) it by using a Command and Control bot to upload the zipped file) to the hacker-controlled Telegram account.

Telegram makes the perfect tool for the bad actors as it’s wildly popular (over 200 million users) and is well-known for its excellent encryption that allows the hackers to cover their tracks.
The malware will also create a scheduled task on all Windows devices it manages to compromise that will allow it to restart itself every minute if the victims discover and kill its process.
Just like Syrk, the malware also creates a scheduled task application that restarts every minute, thus allowing it to avoid detection via Windows Task Manager.
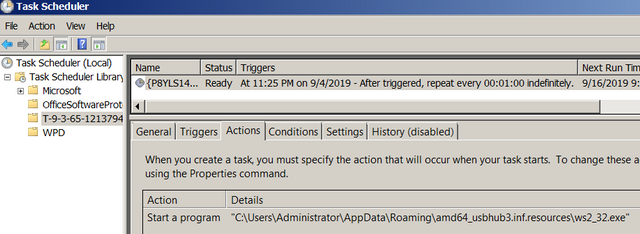
Clipping Process
The malware isn’t just content with stealing your data that will hopefully help them to retrieve your wallet or banking passwords. It also remains behind, by injecting malicious code into your browser lurks deviously in the shadows, until you try to send funds from your crypto wallet again.
The malware has a specific function that checks any copied text on the browser clipboard against a list of regular expressions and supported crypto wallets (e.g. any alphanumeric data that fits a pattern matching specific cryptocurrency addresses).
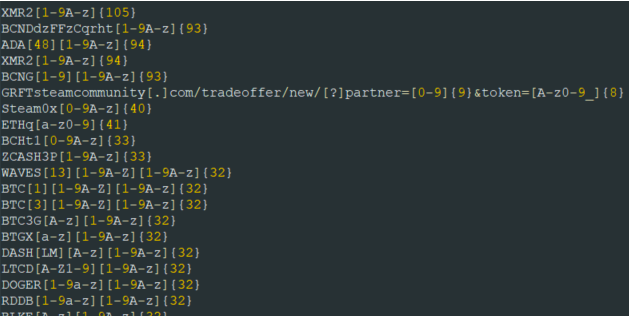
It then replaces the correct clipboard data with a hacker-owned wallet address, tricking senders into unwittingly transferring funds to the bad actor instead of the intended recipient.
One of the malware wallets has already accumulated $9000 by the middle of September, according to researchers.
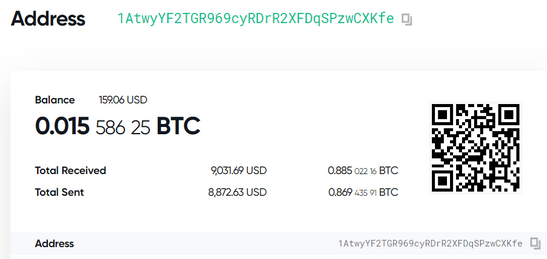
(source: Juniper Network)
What cryptocurrencies does Masad target?
Below is a list of coin and wallet information that Masad tries to clip:
| Monero | Bitcoin Cash | Litecoin | Neo |
| ADA | ZCASH | DogeCoin | Stratis |
| Bitcoin | Waves | Reddcoin | Qtum |
| Bytecoin | Bitcoin | Black Coin | VIA |
| Steam Trade Link | Bitcoin Gold | Emercoin | Lisk |
| Ethereum | Dash | Ripple (XRP) | Payeer |
| NEO | Stratis | Qtum | Web Money |
| VIA | List | Yandex Money | QIWI Pay |
How to remove Masad Stealer
Unlike the Syrk ransomware application that is easy to neutralize due to its fixed known previous iteration HiddenCry, the Masad spyware is harder to eliminate, and prevention might be easier than the cure.
Juniper believes that the Masad Trojan spyware is an “active and ongoing” threat, with C2 bots currently still proliferating and transmitting data and the application still for sale on the Darknet.
The security experts recommend a Next-Generation Firewall (NGFW) that can identify and block the Telegram protocol, and Advanced Threat Protection that can pick up and neutralize Masad in other ways.
Juniper also offers its own protection, a firewall that stops Masad from connecting with the C2 bot and preemptively stops the downloading of any executable file. To learn more about their solution, you can visit their site.
Conclusion
This latest malware application once again demonstrates the increasing range of deadly sophisticated security threats that hackers savvily use to steal cryptocurrency from unsuspecting users. Bad actors are grouping together on the Darknet and often recycle previously released malware, update it and then send it back into the wild, frequently finding success with the same techniques as before.

Like we’ve said in previous posts, it’s always a risk to keep your cryptocurrency assets on an Internet-connected device like a computer or mobile phone. In order to safeguard your crypto, it’s vital to make the investment in a dedicated cold storage wallet like the CoolWallet.
Disclaimer: CoolBitX does not endorse and is not responsible for or liable for any content, accuracy, quality or other materials on this page. Readers should do their own research before taking any action.
CoolBitX is not responsible, directly or indirectly, for any damage or loss caused by or in connection with the use of or reliance on any content, goods or services mentioned in this guide.




